Consider the following...
Understanding the risks...
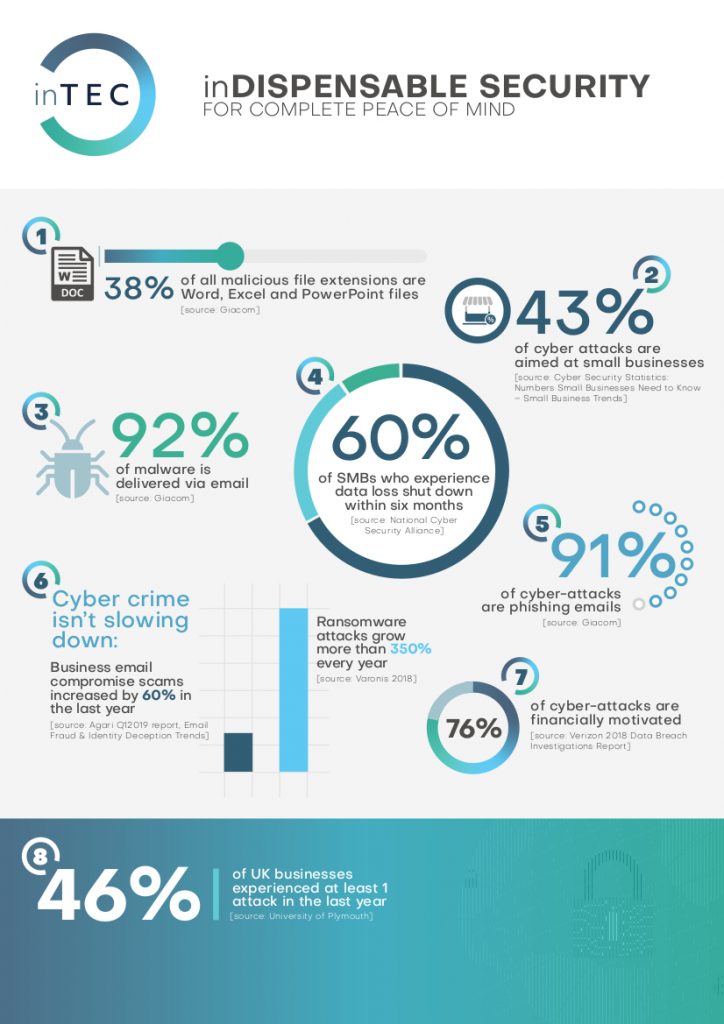
The stats don't lie...
The stats are compelling and speak for themselves.
We’re here to ensure that your business does not become the next victim of a cyber-attack. So, whether you would like us to review the security of your IT systems in general or you are interested in a specific element (e.g., remote worker device security, password protection, data backup…) please get in touch.
We can also help your business obtain Cyber Essentials accreditation (Cyber Essentials helps you to guard against the most common cyber threats and demonstrate your organisation’s commitment to cyber security).
Reduce the risks
As a Microsoft Gold Partner, we can offer helpful advice and implement the right solutions to protect the devices you use and the data you manage in your business every day. We’ll ensure that the services you access are safe. We can also help you to stop unauthorised access to the vast amounts of confidential information you store on your devices and online.

Even with the increase in cyber-attacks over recent years, many small and medium sized businesses are still reluctant to take action by investing in an effective security solution. If your business is one of these, the statistics may help change your mind.
Don’t assume that, if you have a relatively small business, hackers won’t attack. Our experience shows that the opposite is in fact the case: smaller companies are easier to target as they generally do not have appropriate security solutions in place nor a dedicated internal team to manage cyber security. 43% of cyber-attacks are aimed at small businesses!
Our Cyber Security Solutions
A cyber security health check will help you identify your organisation’s weakest security areas. We will recommend appropriate measures to mitigate your risks. The check includes vulnerability scans of critical infrastructure Ips and websites/URLs.
In order for us to perform this basic check we run an NMAP scan and device discovery across your entire network. Using Nessus Professional, a quick uncredentialed scan top 1000 ports against all internal LAN devices as well as all Public IP Addresses. The output is a Nessus report on the security findings of LAN & WAN.
Cyber Essentials is a government-backed, industry supported scheme to help organisations protect themselves against common cyber-attacks. It covers five key technical controls that organisations should have in place to provide a basic level of cyber security.
IASME is the National Cyber Security Centre (NCSC) partner for delivering the Cyber Essentials scheme.
Cyber Essentials is an independently verified self-assessment certification. The self-assessment option gives you protection against a wide variety of the most common cyber-attacks. This is important because vulnerability to simple attacks can mark you out as target for more in-depth unwanted attention from cyber criminals and others.
Certification gives you peace of mind that your defences will protect against the vast majority of common cyber-attacks simply because these attacks are looking for targets which do not have the Cyber Essentials technical controls in place.
Cyber Essentials Plus still has the Cyber Essentials simplicity of approach, and the protections you need to put in place are the same, but this time our licensed assessor will carry out a technical audit of your systems to verify the Cyber Essentials controls are in place.
The testing is not designed for organisations that are likely to be the target of Advanced Persistent Threat (APT) type of attacks but to highlight any potential attacks or weaknesses that may be used by an opportunist attacker.
Penetration testing, also called pen testing or ethical hacking, is the practice of testing a computer system, network or web application to find security vulnerabilities that an attacker could exploit.
Penetration tests assess your systems for potential weaknesses that could result from poor or improper configuration, known and unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures.
An experienced penetration tester will mimic the techniques used by criminals without causing damage, enabling you to address the security flaws that leave your organisation vulnerable
Why conduct a penetration test?
1. Compliance with a regulation or standards, such as the PCI DSS (Payment Card Industry Data Security Standard) or the EU GDPR (General Data Protection Regulation)
2. Ensuring the security of new applications or significant changes to business processes
3. Managing the risks of using a greater number and variety of outsourced services
4. Assessing the risk of critical data or systems being compromised
Fortinet
We work with Fortinet. For over 20 years, their mission has been to secure people, devices, and data everywhere.
They have been a driving force in the evolution of cybersecurity and the convergence of networking and security. Their network security solutions are the most deployed, most patented, and among the most validated in the industry.
Fortinet delivers high-performance network security solutions that protect your network, users, and data from continually evolving threats. Their broad portfolio of top-rated solutions and centralised management enables security consolidation and delivers a simplified, end-to-end security infrastructure.
Watch the short video opposite for more information.
Best Cyber Security Outcomes

Reduce the chances of security breaches within your IT environment

Maintain confidentiality of information

Minimise IT risks, possible damage and consequential costs

Increase trust with respect to partners, customers and the public

Obtain a competitive edge due to recognised standard

Attract new business with the promise you have cyber security measure in place

Obtain a clear picture of your organisations cyber security

Follow a simple, straightforward process

Be listed on the directory of organisation’s awarded certification

Increase your team’s productivity
How can we help?
- Contact us today via phone +353 1 440 3685 or email.
- We’ll be in touch as soon as possible to arrange an inTEC Security Audit;
- After completion, you’ll receive a really useful report of your IT security capabilities and vulnerabilities along with a tailored list of recommendations of how you could improve your security. If you wish to move forward with any of the suggestions, we can make them happen.
For complete peace of mind, protect your organisation’s data, assets, and reputation with inTEC. Let’s talk.